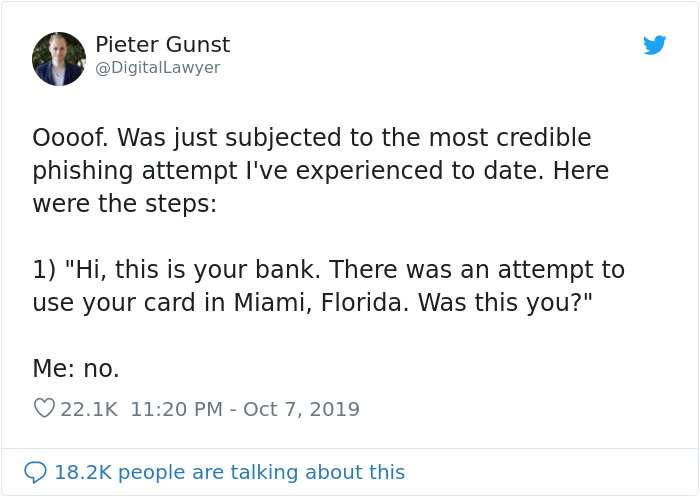
We like to think that we’re immune to scams. However, some of them are so advanced, they can trick even the most vigilant ones. Almost. Pieter Gunst, who has spent years working as a tech lawyer, recently tweeted how he nearly fell for a phishing attempt. Outlining the steps that almost fooled him, he pointed out what everyone should be constantly looking out for in order to keep themselves safe.
More info: Twitter
Image credits: DigitalLawyer
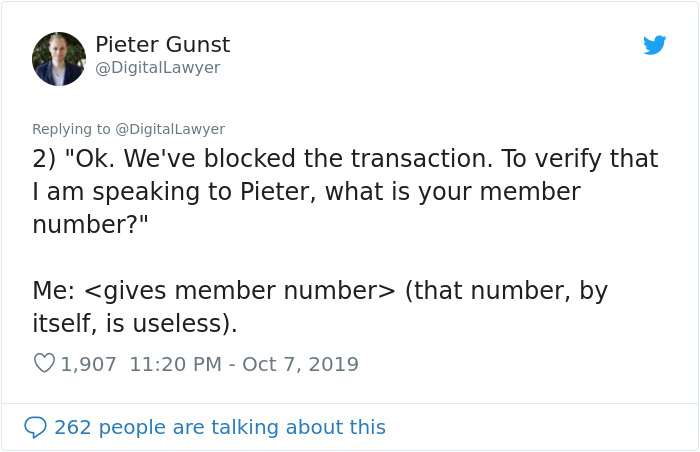
Image credits: DigitalLawyer
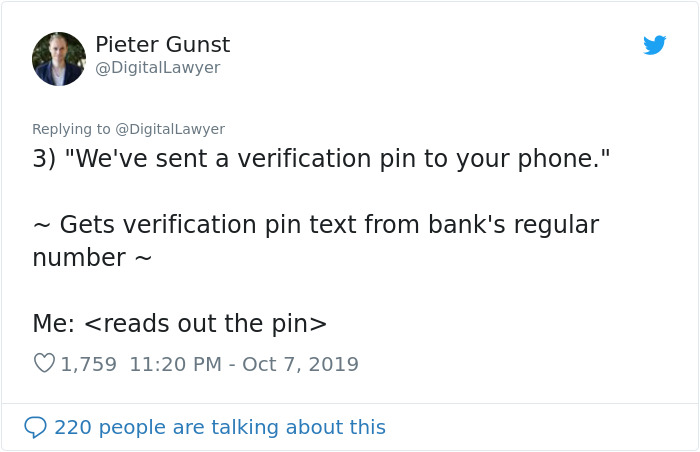
Image credits: DigitalLawyer
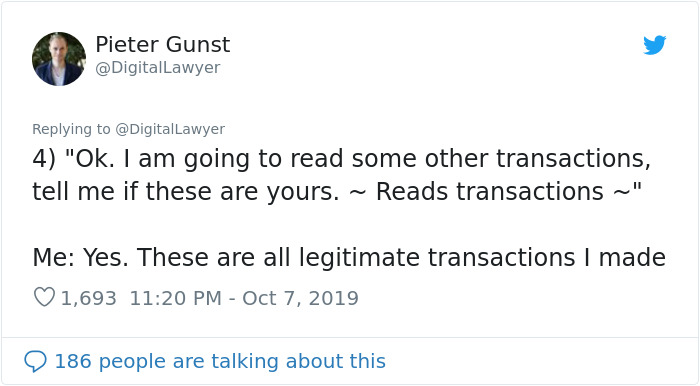
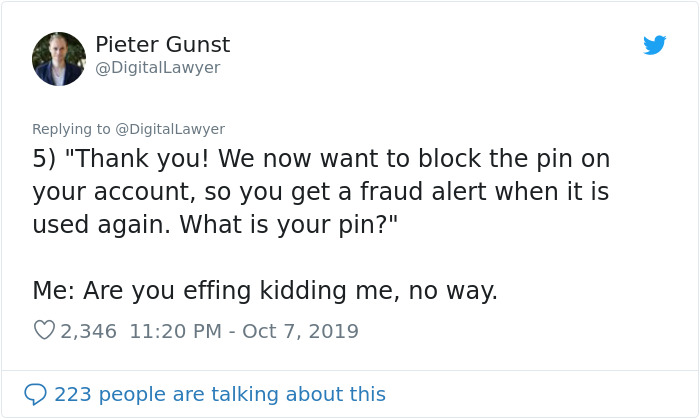
Image credits: DigitalLawyer
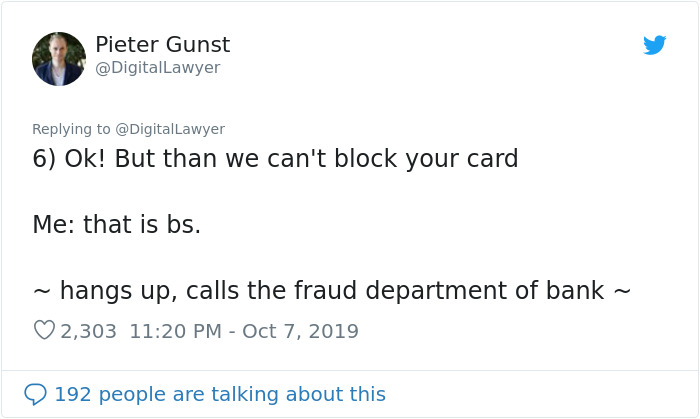
Image credits: DigitalLawyer
Image credits: DigitalLawyer
Image credits: DigitalLawyer
Image credits: DigitalLawyer
Image credits: DigitalLawyer
Microsoft’s security team constantly analyzes trends in cybersecurity threats. The company has been publishing Security Intelligence Reports at least annually since 2006, and they serve as an excellent indicator of these trends. The most recent report indicates that phishing attacks are now the most frequent threat to the cyber landscape, increasing 250% since the publication of the previous report.
To find out more about these illegal activities, Bored Panda spoke with Blue Bridge, a company that provides comprehensive IT services and solutions to large companies and public organizations, including data transmission and cybersecurity.
“Phishing is a method of social engineering, and it’s based on manipulating our emotions,” Blue Bridge cybersecurity expert Ugnius Klevinskas told Bored Panda. Klevinskas said that the reason why it’s so popular among scammers (and will continue to evolve) lies in human nature. “[We’re] curious and trustful, and, on the most part, aren’t ready to think critically in stressful situations.”
Klevinskas also pointed out the findings of various research, saying that neither age, nor education or profession contribute to one’s resistance to social engineering. “Anyone can fall for a similar scam,” he said. “Moreover, when it comes to this particular case, it’s worth highlighting that fake data was combined with the real one. Even though it wasn’t done in a very original manner, the execution was high-quality. It’s clear that the attack was well coordinated and the scammers had been prepared.”
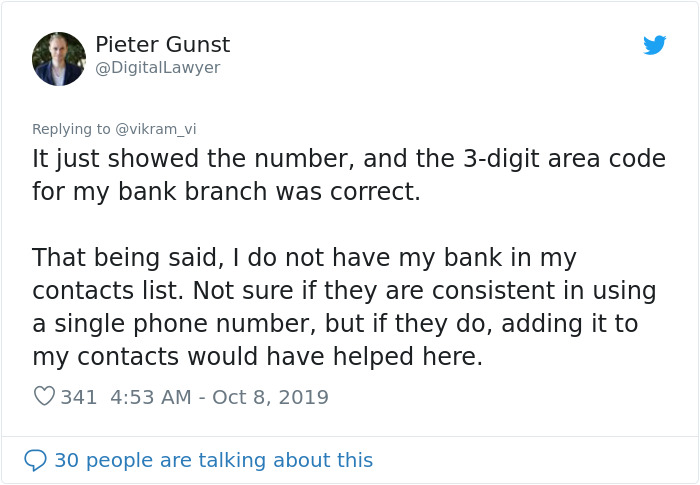
The expert also had some advice on how we all can protect ourselves from something like this: “If somebody asks you to disclose sensitive personal information, be it via e-mail, SMS or phone call, you have to stay vigilant,” Klevinskas said. “The best thing to do is to test the request through another channel. For example, if you received a suspicious e-mail, call the alleged organization or person who sent it and ask them about it. Or, let’s say, a bank employee phoned you, saying you have to provide them your PIN code or other similar info. In such a situation, you should end the conversation and call the bank yourself, making sure there actually is such a person working for that bank.”
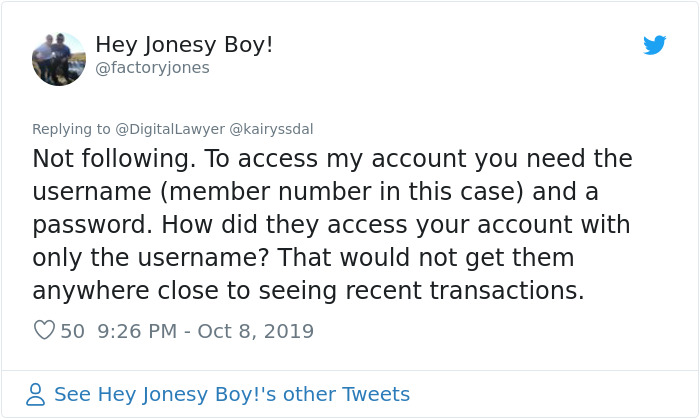
Some people asked Pieter to clarify a few things
Image credits: factoryjones
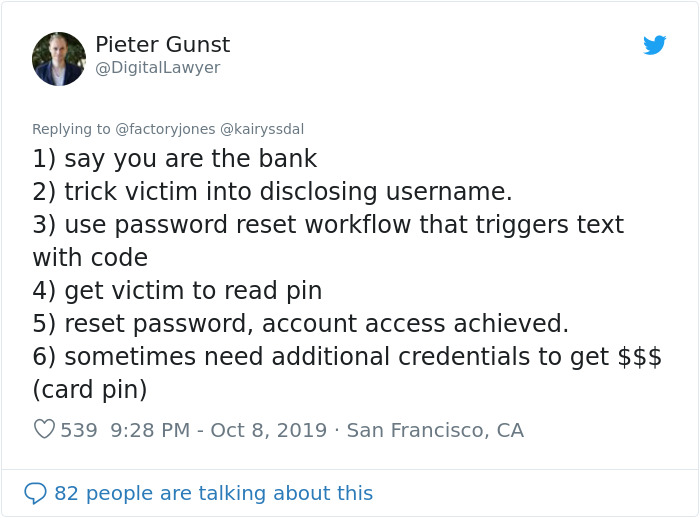
Which he happily did
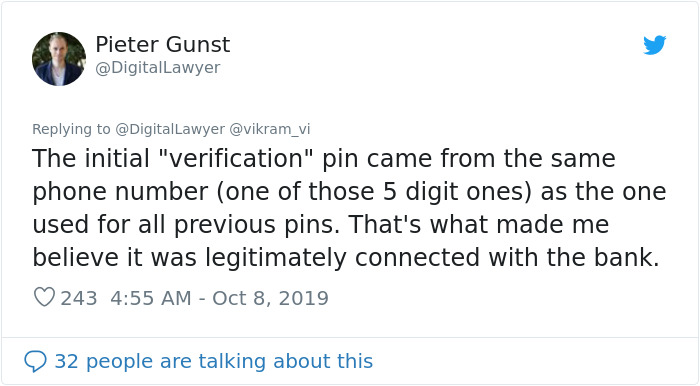
Image credits: DigitalLawyer
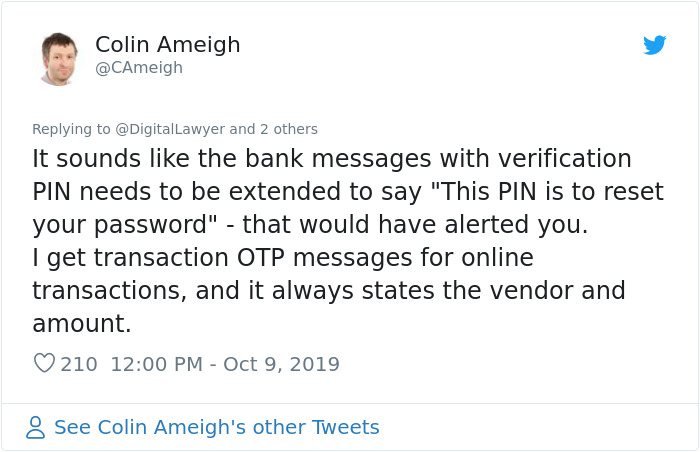
Image credits: CAmeigh
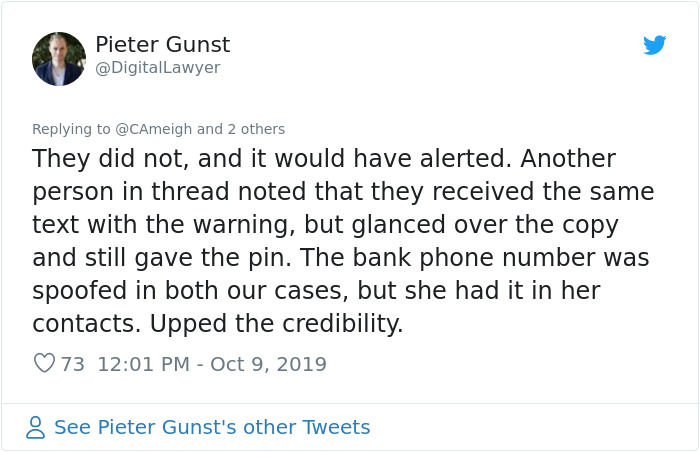
Image credits: DigitalLawyer
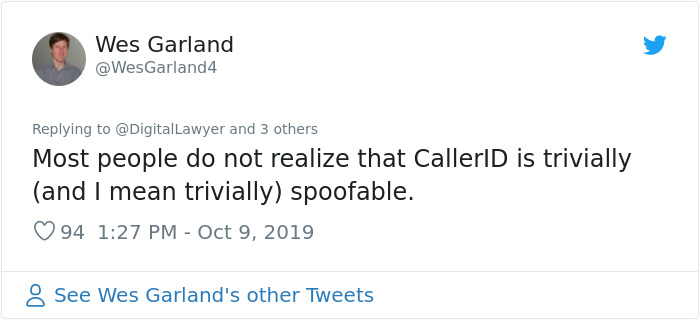
Image credits: WesGarland4
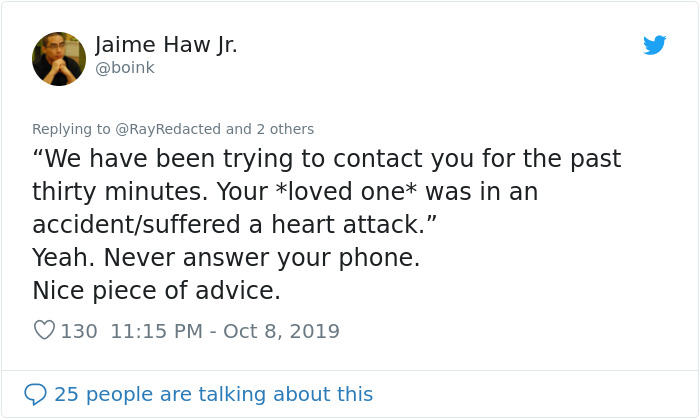
Image credits: boink
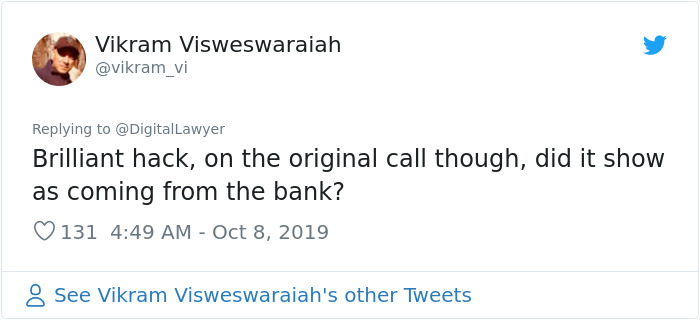
Image credits: vikram_vi
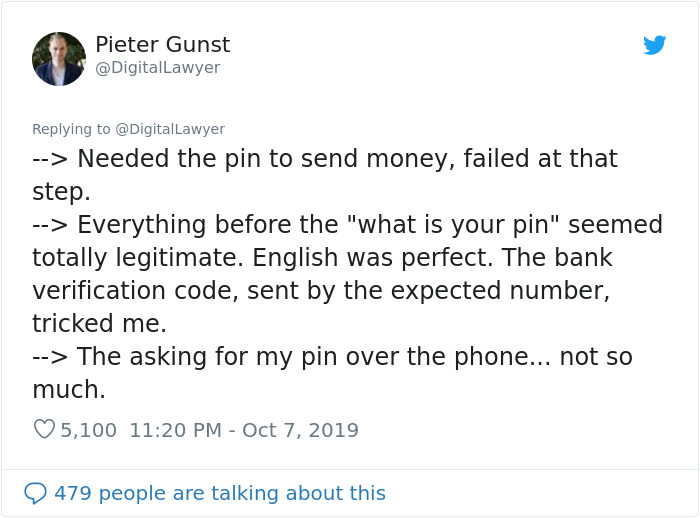
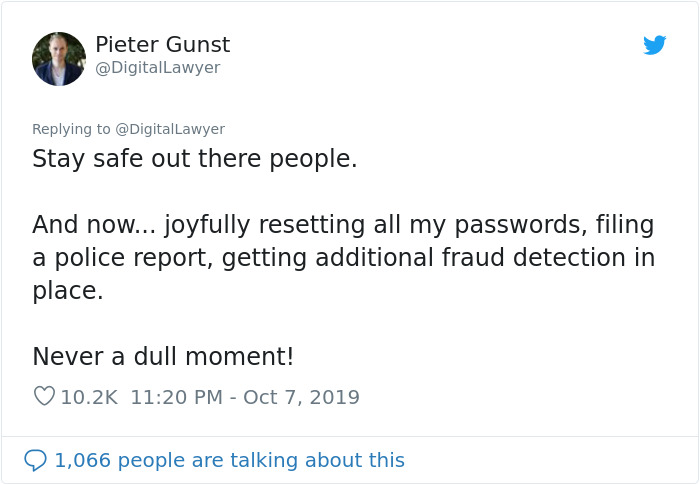
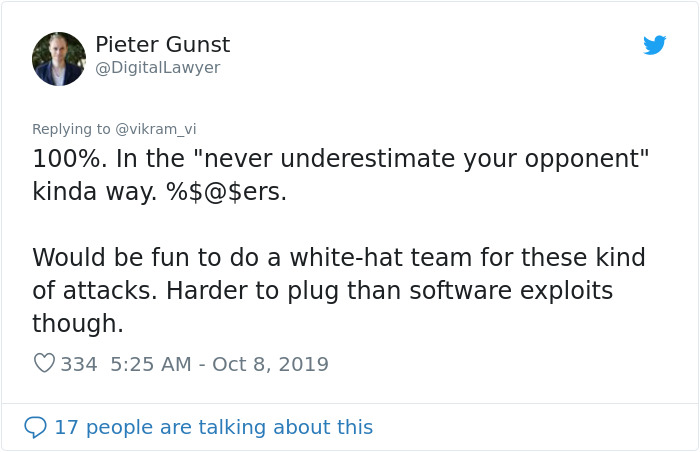
He then continued to explain the situation
Image credits: DigitalLawyer
Image credits: DigitalLawyer
Image credits: DigitalLawyer
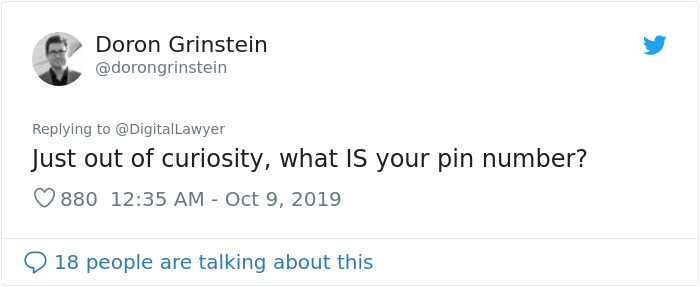
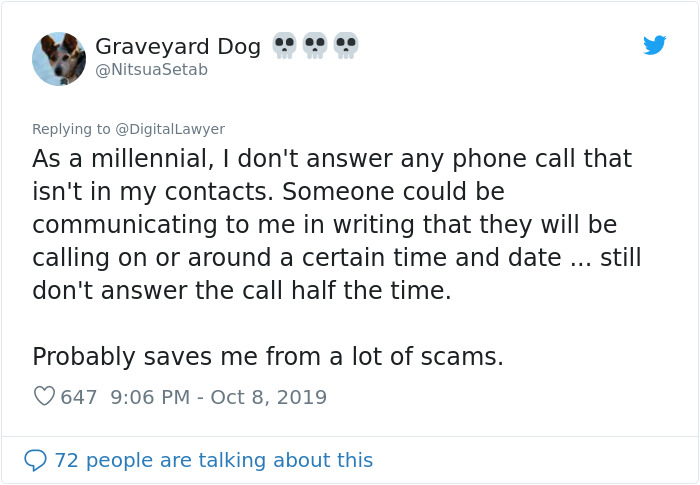
Here’s what others said about it
Image credits: dorongrinstein
Image credits: NitsuaSetab
Image credits: toby_qt

No comments:
Post a Comment